Key Features
- Openvpn For Mac Os
- Viscosity Openvpn Client For Mac
- Download Openvpn Client For Mac
- Best Openvpn Clients For Mac
- Openvpn Download
- L2TP VPN configuration on Mac OS X. DESCRIPTION: SonicWall has the functionality to allow remote users to connect to the network behind the SonicWall using L2TP inbuilt client on MAC OS X using IPSEC VPN protocol. This article focuses on configuration of L2TP VPN on MAC OS X clients to connect to SonicWall UTM appliances.
- On your Mac, choose Apple menu System Preferences, then click Network.
Free download adobe photoshop software. Remote Access VPN ensures that the connections between corporate networks and remote and mobile devices are secure and can be accessed virtually anywhere users are located. A secure remote access solution promotes collaboration by connecting global virtual teams at headquarters, branch offices, remote locations, or mobile users on the go. The instructions below are tested on Mac OS 10.7.3 (Lion). Open System Preferences Network from Mac applications menu. Click the '+' button to create a new service, then select VPN as the interface type, and choose L2TP over IPsec from the pull-down menu. Server Address: E nter the hostname (e.g.com) or the active WAN IP (e.g. Hostname is encouraged instead of active WAN IP.
Cross-Platform.
Viscosity has been designed from the ground up for both macOS and Windows, using native frameworks for perfect integration.
VPN For Everyone.
Completely configure your OpenVPN connections through an intuitive interface, without any need to know complex commands.
Proven Technology.
Viscosity has been protecting users for over a decade, everyone from home users to large enterprise, with regular updates the entire time.
Traffic Statistics.
Viscosity monitors your OpenVPN connections to ensure you know all the important traffic, network and connection details in style.
DNS. Done Right.
Viscosity's powerful DNS system allows you to ensure that all DNS queries use your VPN DNS servers, or only lookups for select domains.
Enterprise Support.
Easily bundle Viscosity with settings and connections so your users are ready to get started. Create simple deployable connection profiles.
Performance Focused.
Every component of Viscosity has been designed to maximise the speed and reliability of your OpenVPN connections.
Script Everything.
Control Viscosity using AppleScript or VBScript, and call custom scripts and actions when a VPN connection changes state.
More. Much More.
Powerful authentication options, connection folders, IPv6, traffic obfuscation, advanced networking, simultaneous connections, and more!
Powerful Connections
Viscosity is a first class VPN client, providing everything you need to establish fast and secure OpenVPN connections on both macOS and Windows.
Viscosity caters to both users new to VPNs and experts alike, providing secure and reliable VPN connections. Whether remotely connecting to your workplace network, home network, VPN Service Provider, or other setup, Viscosity ensures it's done with ease and style.
Stay Informed
Viscosity has a clear and intuitive interface for monitoring your VPN connections. Whether you simply want a quick overview of your OpenVPN connections, or want to drill down to the technical network and encryption details, Viscosity has you covered.
Viscosity's unobtrusive main menu provides an instant overview of your VPN connections, making it a breeze to monitor connection details in real-time. When more information is needed, Viscosity's powerful Details window provides a stylish traffic graph and detailed connection statistics.
Intuitive Editor
Viscosity takes the complexity out of editing VPN connections, while also adding a lot of power at your fingertips. Viscosity's connection editor makes it easy to configure new VPN connections from scratch or edit existing ones. All without needing to know complex commands.
Easily configure everything from network settings to complex multi-factor authentication. Viscosity's powerful DNS modes and traffic routing are also readily accessible to ensure that traffic goes where you want. Power users are also accommodated, with scripting and advanced command support.
New to VPN?
Viscosity makes it easy for users new to VPNs to get started. Its clear and intuitive interface makes creating, configuring, or importing connections a snap. Read our detailed 'Introduction to VPNs' guide for an extensive introduction to VPNs and how to get started using Viscosity.
Experts Welcome
As well as being welcoming to new users, Viscosity caters for power and expert users. Viscosity allows for full control over VPN connections, powerful routing options, running custom scripts, controlling Viscosity using scripting, advanced configuration options, and much more.
Enterprise Ready
Viscosity has been designed for both small business and enterprise. Easily make connection bundles for your users, or completely preconfigure Viscosity with all settings and connections. You can even auto-mount shares and open apps to make life easy for your users.
Expert Features
Obfuscation
Obfuscation helps to prevent your VPN connections from being blocked or throttled by network operators, and Viscosity has powerful traffic obfuscation features built right in. Easily integrate with an existing Obfsproxy server, or run your own, to allow your OpenVPN connections to function even when Deep Packet Inspection (DPI) is being used.
Powerful Editor
Viscosity's connection editor offers unparalleled control over your OpenVPN connections. It allows users unfamiliar with OpenVPN to quickly get started, while also allowing experts to configure all aspects of their connections.
Have you tried it yet with DC yet?When you save a PDF, you can save it into an older version, so the default is to save it into Acrobat 6 or 7 even though you have a newer version. You could try this, but remember that Adobe no longer supports XI.I wonder how that can be true that you need Reader XI (even though they said it). Maybe yes, maybe no. Acrobat reader free for mac. That means that if I have Acrobat XI and save it into Acrobat 7, users need Acrobat 7 or later to view it.
Connection Scripts
Viscosity supports automatically calling your own custom scripts on VPN connection events. Power users can write their own AppleScript, Batch, or VBS scripts to automatically perform almost any action they want. This includes tasks like opening and closing certain applications on connect or disconnect, opening web pages, mounting file shares, or controlling other apps.
Scriptable
Viscosity is fully scriptable, allowing your OpenVPN connections to be controlled using your own custom AppleScript or Batch scripts. It also allows Viscosity to be combined with other third party tools to provide functionality such as automatically when connecting to certain WiFi networks, or when in certain locations.
Complete IPv6 Support
Viscosity has complete IPv6 support. No matter whether you want to connect to your OpenVPN server over an IPv6 network, or have your VPN network support IPv6, Viscosity has you covered. Viscosity's DNS support also fully supports IPv6, including Split DNS.
Connection Folders
Easily group your OpenVPN connections into folders to make them easier to manage. This is particularly useful if you want to share credentials or scripts between multiple VPN connections, such as with a VPN Service Provider.
Full & Split DNS
Viscosity's powerful DNS system goes above and beyond other VPN clients, offering both Full and Split DNS modes. Ensure that your VPN DNS servers are used by default with Full DNS mode, or use Split DNS mode to only use your VPN DNS servers for certain domains.
Native Apps
Viscosity is written using completely native frameworks on both macOS and Windows, letting it perfectly integrate with your operating system and offer top performance. No memory and CPU hungry cross-platform frameworks are used: Viscosity offers a completely native user interface with no bloated web-application frameworks.
Simultaneous Connections
Connect to a single VPN connection at a time, or connect to multiple simultaneously. No need to switch between VPN connections when working with multiple sites remotely: Viscosity lets you connect to them at the same time and correctly routes traffic and DNS requests for each network.
Enterprise Features
Cross-Platform
Viscosity has been developed from the ground up for both macOS and Windows to provide a premier and native experience on both platforms. This makes is easy to deploy a single solution to all of your users, without the expense of having to train support staff and users in the use of multiple clients for different platforms.
Deployment Ready
Viscosity has been designed to be easy and straightforward to deploy in managed environments. Easily package Viscosity with VPN connections and settings and deploy it using tools such as Mobile Device Management (MDM) or Group Policy (GPO). Or use third-party deployment software such as Munki or Jamf to deploy Viscosity and offer self-service installation.
Bundle Connections & Settings
Viscosity can be bundled together with connections and settings, so Viscosity is ready to go as soon as it is installed, with no configuration required by end users. Viscosity also provides a number of extra customisable settings to help Viscosity fit into your networking and security environment, including the ability to change Viscosity's username and password storage behaviour and global scripting.
Supported Software
Viscosity is commercially supported software. We stand behind our products: if you run into trouble, need help, or would like advice, we are only an email away. There is no need to try your luck on mailing lists, or attempt to hunt down developers for support.
Ease of Use
Viscosity has a clear and intuitive interface for controlling VPN connections, allowing users new to VPNs and Viscosity to easily use OpenVPN on both macOS and Windows. Viscosity's Details window provides a simple interface for obtaining connection statistics and diagnostic information to pass on to support staff.
Reliability
Viscosity is in use everywhere, from large enterprise to small business, schools, universities, at home and on the road. You can use deploy Viscosity with piece of mind that it has been constantly tested and refined for almost any network environment. Viscosity has been constantly refined to automatically adjust to a huge variety of network conditions to ensure your user's VPN connections are reliable and trouble-free as possible.
Connection Profiles
Viscosity connection packages can be exported and distributed to users, providing an easy mechanism to supply users with connections (and all associated certificates, keys, and scripts) in a single package when providing a fully bundled version of Viscosity is not suitable.
Standard & Admin User Support
Viscosity can run under both administrator accounts and standard user accounts, for both macOS and Windows. This makes deploying Viscosity to machines that are not department controlled/imaged (such as machines at a user's home) much easier and simpler.
Smartcard, Token, & U2F Support
Viscosity supports PKCS#11 and FIDO Universal 2nd Factor (U2F) authentication options, allowing your users to use devices like smartcards and eTokens for authentication. You can use these devices as the sole method for authentication, or combine them with other authentication methods to create two-factor, or even three-factor, authentication. This helps you meet strict security polices, such as the Payment Card Industry Data Security Standard (PCI DSS).
Automatic Actions
Viscosity allows calling custom scripts before a connection connects, when it connects, or when it disconnects. This allows common tasks to be easily automated, such as connecting to file servers and mounting shares, opening web pages, opening applications, controlling other applications, and displaying messages to the user. Viscosity supports AppleScript scripts under macOS, and both Batch (.bat) and Visual Basic/VBS (.vbs) scripts under Windows.
Conditional Connections
Viscosity's conditional connections mechanism makes it easy to have Viscosity only connect to a VPN server on certain networks, or only in certain environments. A custom script can check for certain conditions (such as the wireless network the machine is connected to, the IP address, location, etc.) and decide whether to allow or terminate the connection attempt.
Big shout-out to @sparklabs! Viscosity is excellent with constant updates and flawless operation. #wortheverypenny #bestvpnclient
@daveprovine | Twitter
If you're using #OpenVPN and you're not using #Viscosity then you're doing it wrong :) @sparklabs - Thanks for an awesome app!
@systemcentersyn | Twitter
Just wanted to say that Viscosity is a great app. I'm very happy with its performance, ease of use, reliability, and design.
@CyborgInteract | Twitter

Every professional VPN solution I've used for Mac can't hold a candle to @sparklabs's Viscosity. Its by far the best
@JonoH | Twitter
Hat tip to @sparklabs for Viscosity. It's the OpenVPN client I'd write if I had to. Which I don't, because they wrote it.
@landonfuller | Twitter
I'm really pleased with Viscosity. It's an extremely elegant #Mac #OpenVPN client solution.
@noviantech | Twitter
PSA: The Viscosity OpenVPN client from @sparklabs is awesome - regularly updated and a great value. Recommended!
@_4bdi3l | Twitter
Love Viscosity from @sparklabs. Easy install, it just works. Reliable OpenVPN connections for Windows and Mac.
@clemensmol | Twitter
I just downloaded Viscosity after toiling with the various OpenVPN offerings.. I must say, I have fallen in love! Keep it up!
@MilesKjeller | Twitter
All Features
Authentication
- Username & Password
- Public Key Infrastructure (PKI) & PKCS#12
- Shared Secret
- PKCS#11 Token & Smartcard
- FIDO Universal 2nd Factor (U2F)
- One Time Password (OTP)
- Dynamic & Static Two Factor
Network
Openvpn For Mac Os
- Simultaneous Connections
- Full & Split DNS Modes
- Connect via HTTP or SOCKS Proxy
- Traffic Obfuscation
- DHCP IP, DNS, And Route Assignment
- Complete IPv4 and IPv6 Support
- Automatic & Manual Proxy Settings
- Powerful Traffic Routing Options
- Intelligent Server Selection & Fallback
Interface
- Powerful Connection Editor
- Traffic Graph & Statistics
- Unobtrusive Status Icon & Menu
- Customisable Menu Icons
- Customisable Menu Quick Statistics
- Connection Folders & Shared Credentials
- OpenVPN Version Selection
Performance & Integration
- Native Implementation for Each Platform
- Low CPU & Memory Usage
- Reliable OpenVPN Connections
- Automatically Disconnect on Inactivity
- Automatically Reconnect on Disconnect
- Automatically Reconnect on Network Availability
- Automatically Disable Time Machine Backups
Security
- Latest Cipher & Digest Support
- Sandboxed OpenVPN & Scripts
- Keychain & Windows Password Store Integration
- IPv6 Leak Protection
Enterprise
- Bundling Connections & Preferences
- GPO Group Policy Deployment
- Connection Importing & Exporting
- Admin Rights Not Required for User Operation
Advanced
- Conditional Connections
- Control Viscosity using AppleScript
- Control Viscosity using Scripts or Command Line
- Run Scripts on Connection Events
- Advanced Configuration Commands
Platform Screenshots
Viscosity for macOS and Windows
Download Viscosity now to trial it for 30-days with no purchase necessary and no limitations. Purchase Viscosity to remove the 30-day trial limitation and help support its development. Viscosity is a one-time purchase, with no subscriptions or recurring fees.
Release Notes | Volume Licenses & Discounts | Upgrades & Extensions
The purpose of this document is to lead the users to configure theirs OpenVPN clients to access to a VPN server. We will see how to install and configure the most used OpenVPN's GUI for Microsoft Windows, Linux, Mac OS X and Windows Mobile for Pocket PC. At the end of the document we will learn to use the OpenVPN's command line interface. This last possibility is useful, because the openvpn command, which you can execute by using the prompt (Unix Shell or Windows Prompt) accepts the same parameters and has the same behavior regardless from which Operating System you use. In addition, you could use the openvpn command in a script to automatically start the VPN connection.
More precisely, we will see how to access to a VPN server builded with ZeroShell and configured with the default parameters. To obtain an OpenVPN server with the default behavior, you only need, after you have activated Zeroshell on your network, to enable the OpenVPN service by clicking on the Enabled flag in the [VPN]->[OpenVPN] section of the Zeroshell's web interface. By default, the OpenVPN server of Zeroshell listens on the port 1194/TCP with TLS/SSL encryption and LZO compression enabled. The user authentication well be checked by using username and password credentials, but we will try the X.509 authentication as well.
For further details about the configuration of an OpenVPN server builded with ZeroShell, you can read the 'An OpenVPN server using Zeroshell' how-to.
The sections in which this how-to is divided are as follows below. Keep in mind that the first section, which is related to the configuration file of OpenVPN, it is common to the other ones, because the configuration file do not depend on the GUI or Operating System that you use.
The configuration file of OpenVPN

Every professional VPN solution I've used for Mac can't hold a candle to @sparklabs's Viscosity. Its by far the best
@JonoH | Twitter
Hat tip to @sparklabs for Viscosity. It's the OpenVPN client I'd write if I had to. Which I don't, because they wrote it.
@landonfuller | Twitter
I'm really pleased with Viscosity. It's an extremely elegant #Mac #OpenVPN client solution.
@noviantech | Twitter
PSA: The Viscosity OpenVPN client from @sparklabs is awesome - regularly updated and a great value. Recommended!
@_4bdi3l | Twitter
Love Viscosity from @sparklabs. Easy install, it just works. Reliable OpenVPN connections for Windows and Mac.
@clemensmol | Twitter
I just downloaded Viscosity after toiling with the various OpenVPN offerings.. I must say, I have fallen in love! Keep it up!
@MilesKjeller | Twitter
All Features
Authentication
- Username & Password
- Public Key Infrastructure (PKI) & PKCS#12
- Shared Secret
- PKCS#11 Token & Smartcard
- FIDO Universal 2nd Factor (U2F)
- One Time Password (OTP)
- Dynamic & Static Two Factor
Network
Openvpn For Mac Os
- Simultaneous Connections
- Full & Split DNS Modes
- Connect via HTTP or SOCKS Proxy
- Traffic Obfuscation
- DHCP IP, DNS, And Route Assignment
- Complete IPv4 and IPv6 Support
- Automatic & Manual Proxy Settings
- Powerful Traffic Routing Options
- Intelligent Server Selection & Fallback
Interface
- Powerful Connection Editor
- Traffic Graph & Statistics
- Unobtrusive Status Icon & Menu
- Customisable Menu Icons
- Customisable Menu Quick Statistics
- Connection Folders & Shared Credentials
- OpenVPN Version Selection
Performance & Integration
- Native Implementation for Each Platform
- Low CPU & Memory Usage
- Reliable OpenVPN Connections
- Automatically Disconnect on Inactivity
- Automatically Reconnect on Disconnect
- Automatically Reconnect on Network Availability
- Automatically Disable Time Machine Backups
Security
- Latest Cipher & Digest Support
- Sandboxed OpenVPN & Scripts
- Keychain & Windows Password Store Integration
- IPv6 Leak Protection
Enterprise
- Bundling Connections & Preferences
- GPO Group Policy Deployment
- Connection Importing & Exporting
- Admin Rights Not Required for User Operation
Advanced
- Conditional Connections
- Control Viscosity using AppleScript
- Control Viscosity using Scripts or Command Line
- Run Scripts on Connection Events
- Advanced Configuration Commands
Platform Screenshots
Viscosity for macOS and Windows
Download Viscosity now to trial it for 30-days with no purchase necessary and no limitations. Purchase Viscosity to remove the 30-day trial limitation and help support its development. Viscosity is a one-time purchase, with no subscriptions or recurring fees.
Release Notes | Volume Licenses & Discounts | Upgrades & Extensions
The purpose of this document is to lead the users to configure theirs OpenVPN clients to access to a VPN server. We will see how to install and configure the most used OpenVPN's GUI for Microsoft Windows, Linux, Mac OS X and Windows Mobile for Pocket PC. At the end of the document we will learn to use the OpenVPN's command line interface. This last possibility is useful, because the openvpn command, which you can execute by using the prompt (Unix Shell or Windows Prompt) accepts the same parameters and has the same behavior regardless from which Operating System you use. In addition, you could use the openvpn command in a script to automatically start the VPN connection.
More precisely, we will see how to access to a VPN server builded with ZeroShell and configured with the default parameters. To obtain an OpenVPN server with the default behavior, you only need, after you have activated Zeroshell on your network, to enable the OpenVPN service by clicking on the Enabled flag in the [VPN]->[OpenVPN] section of the Zeroshell's web interface. By default, the OpenVPN server of Zeroshell listens on the port 1194/TCP with TLS/SSL encryption and LZO compression enabled. The user authentication well be checked by using username and password credentials, but we will try the X.509 authentication as well.
For further details about the configuration of an OpenVPN server builded with ZeroShell, you can read the 'An OpenVPN server using Zeroshell' how-to.
The sections in which this how-to is divided are as follows below. Keep in mind that the first section, which is related to the configuration file of OpenVPN, it is common to the other ones, because the configuration file do not depend on the GUI or Operating System that you use.
The configuration file of OpenVPN
Because the large number of parameters you can define either in the configuration file or in the command line, you could configure OpenVPN in many different manners. In any case, to obtain a connection with a Zeroshell VPN server, you only need to define a small number of them in your client's configuration file. In order to further simplify the configuration of the OpenVPN client, you could download an example of configuration file by clicking on the link OpenVPN Client configuration.The file has comments that explain the meaning of the parameters, but only 2 of them you surely need to change to obtain a VPN connection with Zeroshell:
- remote zeroshell.example.com 1194You have to replace zeroshell.example.com with the hostname or the IP address of the OpenVPN server. The Zeroshell's default configuration requires that the OpenVPN service listens on the port 1194/TCP and therefore you must not modify the second parameter (1194).
- ca CA.pemThe ca parameter specify a file (in PEM format), that contains the X.509 Certification Authority with which the server certificate has been signed. To get the CA's X.509 certificate, you only need to click on the CA hyperlink in the Zeroshell's login page. If you save the CA's certificate with the name CA.pem in the same directory of the configuration file, the you do not need to change the parameter. Otherwise, you must specify the absolute path of the file.
Keep in mind that certificate of the Certification Authority is required also if you do not use the X.509 client authentication but the 'Only Password' authentication (Default in Zeroshell).
Notice, that you will always have to manually edit the configuration file. This is because the Graphical User Interfaces that we are going to learn do not assist you in the creation and maintenance of the OpenVPN's configuration. They only help you to connect and disconnect the VPN, and ask for the username and password if they are required.
OpenVPN GUI for Windows
To install OpenVPN GUI for Windows on a Microsoft Windows XP 32/64 bits, follow the steps below:
- Download the installer from the URL https://openvpn.net/index.php/open-source/downloads.html. Choose he file that contains the GUI and the OpenVPN software already included;
- Start with the installation. Select the default options and confirm the installation of the TAP-Win32 Adapter V8 device (it is a Virtual Ethernet interface used by OpenVPN).
When the Installer has finished to work, the TrayBar contains the VPN icon with two red terminals and the Earth Globe symbol. Such terminals are yellow when OpenVPN is trying to establish the connection and they are green when you are finally connected with the VPN; - In the Windows Start Menu, click on [Start]->[All Programs]->[OpenVPN]->[OpenVPN configuration file directory]. You will be able to explore the folder:
C:Program FilesOpenVPNconfig
in which you must copy the files zeroshell.ovpn that contains the OpenVPN configuration and CA.pem that is the X.509 Certification Authority certificate. You can look at the previous section for details on how to obtain these files;
- Edit the file zeroshell.ovpn and replace zeroshell.example.com with the hostname or the IP address of the OpenVPN router;
- At this point, you have finished to install and configure the OpenVPN client and its GUI. With a double-click on the OpenVPN icon in the Tray Bar, you can try to start the VPN connection. A dialog box will appear and request you to type the username and the password to be authenticated (look at the note *). If the authentication step is successfully completed, then the VPN connection will be established and the two yellow terminals will become green.
By right-clicking on the OpenVPN icon in the Traybar appears a contextual menu with several useful options: Connect, Disconnect, Show Status, View Log, Edit Config, Proxy Settings. Particularly useful to solve connection problems is the item View Log that allows to know the reason of the failures.
If instead the VPN is connected (the two terminals are green), but you are not able to reach the remote LAN or Internet using the Virtual Private Network, then you should use the ipconfig /all command from the Windows Prompt. Here there is an example of the lines of output about the virtual Ethernet interface:
To be sure that the IP traffic is actually routed across the VPN and hence encrypted, you must check that the IP Address and the Default Gateway assigned to the TAP Virtual Interface belong to the remote LAN you are connected. To better check this condition, you could also use the tracert /d command: if the first hop that is printed belongs to a subnet of the remote LAN then your VPN works fine and the traffic that reaches the remote site is encrypted across Internet.
Tunnelblick for Mac OS X
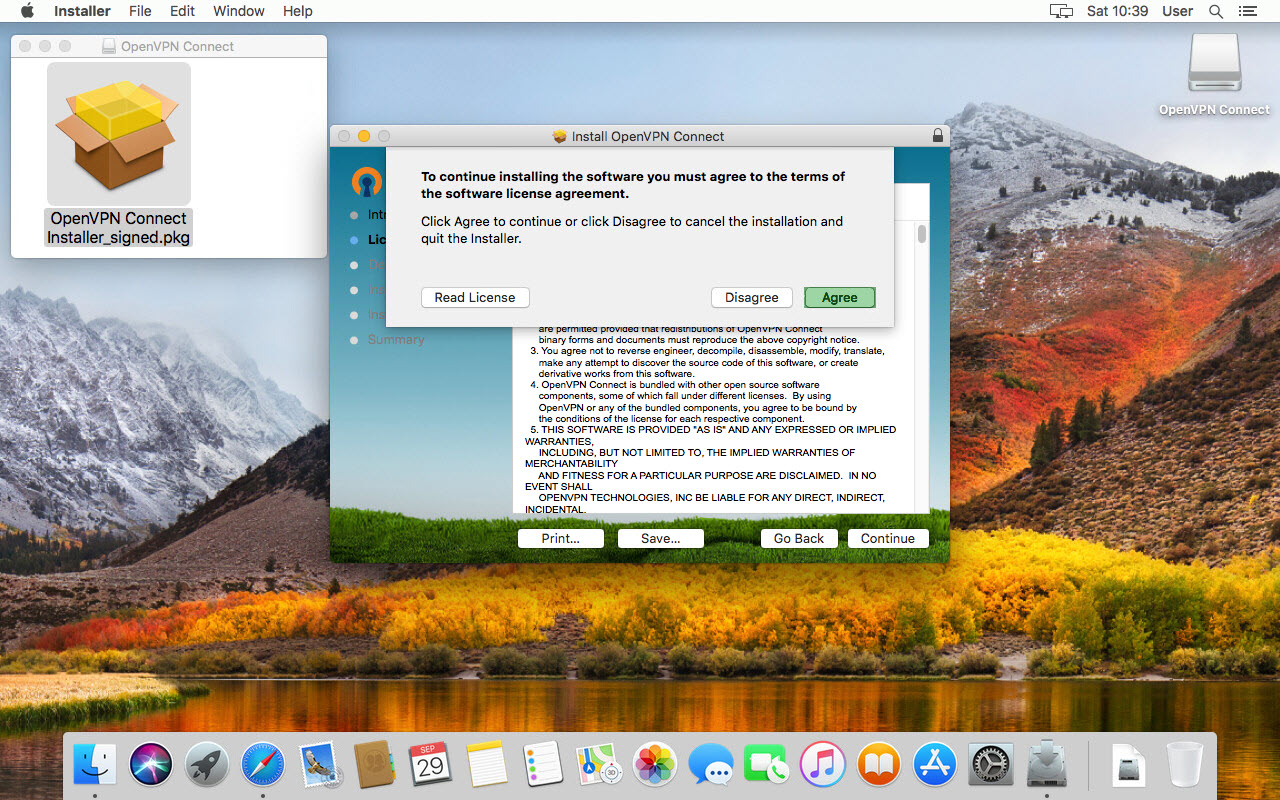
A Graphical User Interface for OpenVPN on Mac OS X is a package called Tunnelblick. To install this GUI, follow the steps below:
- Download the package from the site https://tunnelblick.net. It is a disk image file which contains the GUI, the OpenVPN software, and some documentation;
- Double-click on the .dmg file;
- A Finder window appears on the desktop. The window contains Tunnelblick.app. Double-click it;
- A dialog box will ask you to confirm that you wish to install Tunnelblick.app to Applications. Click the Install button;
- A dialog box will ask if you wish to launch Tunnelblick. Click the Launch button;
- A dialog box will ask for an administrator username/password to secure Tunnelblick. Type administrator credentials and click the OK button;
- A dialog box will appear welcoming you to Tunnelblick. Click the Create and open configuration folder button;
- A Finder window will open with the configuration folder. The window will contain only an alias to Tunnelblick.app. Drag the files zeroshell.ovpn and CA.pem to the window. If you don't know how to obtain these two files, please read the section The configuration file of OpenVPN
- Double-click on the Launch Tunnelblick alias;
- A dialog box will appear asking if you wish to check for updates to Tunnelblick automatically. Click Check Automatically or Don't Check, as you prefer;
- Tunnelblick is now installed. Its icon appears near the clock. Click on the Tunnelblick icon, then select the [Details…] item;
- Click on the Edit Configuration button in the dialog box which appears. Replace zeroshell.example.com with the hostname or the IP address of the VPN server. Save the configuration file and quit;
- Start the VPN connection by clicking on the Tunnelblick icon near the clock and selecting the Connect ‘Zeroshell' item;
- A dialog box will appear asking for an administrator username/password to secure the configuration file. Type administrator credentials and click OK;
- A dialog box will appear asking for the VPN username and password. Type the VPN username and password and click 'OK' (look at the Note *). You may save them in the Keychain by putting a check in the check box.
In the case in which there are connection problems, select the item [Details…] to check the OpenVPN's log messages.
If you want to verify that the IP address that the VPN server has assigned to you, actually belongs to the remote LAN with which you are connected, you have to open a Mac OS X Terminal and at the prompt of the shell type the command:
ifconfig tap0
the result looks like this:
The line that starts with inet show you that the VPN IP address assigned to you is 192.168.250.1 (by default Zeroshell issues IP addresses which belong to the subnet 192.168.250.0/24 with 192.168.250.254 as Default Gateway). To be sure that the IP traffic is actually routed across the VPN and hence encrypted, you must check that the IP Address and the Default Gateway assigned to the TAP Virtual Interface belong to the remote LAN you are connected. To better check this condition, you could also use the traceroute -n command: if the first hop that is printed belongs to a subnet of the remote LAN (192.168.250.254 by default) then your VPN works fine and the traffic that reaches the remote site is encrypted across Internet.
KVpnc for Linux
KVpnc is a Linux frontend that is able to manage many type of VPN clients such as: Cisco VPN, IPSec, PPTP, OpenVPN, L2TP. It has also the SmartCard support. Obviously, in this document we will see only the installation and configuration of KVpnc related to OpenVPN. Binary packages of KVpnc exist for many Linux distributions such as the RPM for Suse and Fedora. For Ubuntu and Kubuntu (and other Debian derived distributions), you can easily install KVpnc with OpenVPN by using the commands:
sudo apt-get install openvpn
sudo apt-get install kvpnc
Notice that, unlike the other GUIs, the packages of KVpnc do not include OpenVPN, but you must install it alone. In order to make this document regardless of the Linux Distribution used, we will build and install KVpnc by compiling the source code, but if a binary package exists for your Linux distribution, you should prefer to use it without waste your time in the building process.
Because KVpnc uses the QT libraries, their presence and their include files are required in the build process. In the next steps, we will assume that the OpenVPN package is already installed. If you are not in this situation, you should read the section Build and install OpenVPN to learn to install OpenVPN.
Now we are ready to install and configure KVpnc by following the steps given bellow:
- Download the KVpnc's source code package from the web page https://userbase.kde.org/KVpnc. We'll use the release 0.8.9 of KVpnc, but you should get the latest one;
- Extract the source code by using the command:
tar xvfj kvpnc-0.8.9.tar.bz2 - Build and install KVpnc by following this steps:
cd kvpnc-0.8.9
./configure
make
sudo make installFor some Linux distributions, the ./configure command could be unable to locate the QT libraries. In this case, you must find out where the include files and the libraries are located and specify the paths by adding the parameters –with-qt-includes=/usr/lib64/qt-3.3/include/ –with-qt-libraries=/usr/lib64/qt-3.3/lib/ to the ./configure. Of course, you should replace the path /usr/lib64/qt-3.3/ with the one in which the QT libraries are located in your Linux system; - Make the directory /etc/openvpn/ with the command sudo mkdir /etc/openvpn and copy in the new directory the files zeroshell.ovpn and CA.pem. How to obtain such files is described in the section The configuration file of OpenVPN;
- To use KVpnc with unprivileged users the sudo command is required and the line
ALL ALL=NOPASSWD:/usr/bin/kvpncmust be added at the end of the file /etc/sudoers (notice that you need to have administrator privileges to change this file). After that, you are able to launch the kvpnc process by using the command:
sudo /usr/bin/kvpnc
In this manner, the kvpnc will have the root‘s privileges needed to create the tap0 Virtual Ethernet Interface and add the static routes in the Kernel routing table;
Viscosity Openvpn Client For Mac
- Import the profile that allow you to create a VPN with Zeroshell by using the following command:kvpnc –openvpnimport=/etc/openvpn/zeroshell.ovpnBy using the Profile Manager that appears, make the following configuration changes:
- From the General options, insert in the VPN gateway field the IP address or the hostname of the VPN server;
- From the OpenVPN options, check that the Authentication method is the SHA1 hash function and not MD5 one;
Press [Apply] and then [Ok] on the Profile Manager. After that, save the Zeroshell profile using the [Profile]->[Save Profile…] menu item and close kvpnc interface with [File]->[Quit] menu item;
- Start the KVpnc GUI with the command sudo /usr/bin/kvpnc and click the [Connect] button to establish the VPN connection. At this point, you are requested for the username and the password to use to authenticate your identity against the VPN server (look at the Note *).
If you want to verify that the IP address that the VPN server has assigned to you, actually belongs to the remote LAN with which you are connected, you have to open a terminal and at the prompt of the shell type the command:
ifconfig tap0
the result looks like this:
The line that starts with inet show you that the VPN IP address assigned to you is 192.168.250.50 (by default Zeroshell issues IP addresses which belong to the subnet 192.168.250.0/24 with 192.168.250.254 as Default Gateway). To be sure that the IP traffic is actually routed across the VPN and hence encrypted, you must check that the IP Address and the Default Gateway assigned to the TAP Virtual Interface belong to the remote LAN you are connected. To better check this condition, you could also use the traceroute -n command: if the first hop that is printed belongs to a subnet of the remote LAN (192.168.250.254 by default) then your VPN works fine and the traffic that reaches the remote site is encrypted across Internet.
OpenVPN for Windows Mobile on Pocket PC
OpenVPN for Pocket PC is still an Alpha release, but it worked fine during the test on Microsoft Windows Mobile v5.0 installed on a PDA i-Mate JASJAR (equivalent to a HTC Universal Qtek 9000). Before seeing how to install and configure this software, notice that you will have to manually modify the OpenVPN configuration file and therefore you should use Microsoft ActiveSync for editing from your Personal Computer. Another solution could be to install on your PPC the Total Commander CE that is a Freeware File Manager for Pocket PC, available at the URL http://www.ghisler.com/pocketpc.htm. This filemanager includes an Editor which allows you to edit the OpenVPN configuration file directly from your Palm Device.
Now, follow the steps below to install OpenVPN for Windows Mobile on your Pocket PC:
- Download the OpenVPN for Pocket PC from the site http://ovpnppc.ziggurat29.com/ovpnppc-main.htm. There are two type of file: the .exe format that you can install from your Personal Computer connected to the PPC with ActiveSync; the .cab format that you can directly install on your Pocket PC. Pick the package in the format that you prefer and install it.
- Supposing that you have installed OpenVPN for Pocket PC in the directory Program FilesOpenVPN of the device's memory, copy the files zeroshell.ovpn and CA.pem in the folder Program FilesOpenVPNconfig. To know how to obtain these two files, read the section The configuration file of OpenVPN;
- Edit the configuration file Program FilesOpenVPNconfigzeroshell.ovpn to connect to your OpenVPN server:
- Replace zeroshell.example.com with the IP address or the hostname of the OpenVPN server;
- Replace CA.pem with the path of the file that contains the Certification Authority. In your case the path is:ca 'Program FilesOpenVPNconfigCA.pem'Notice the double quotes and the double backslashes that are requested by the syntax of this parameter;
- Click on the icon of OpenVPN and from the submenu [Start from Config.] select zeroshell. At this point you are requested for the Username and Password (look at the Note *). If the client is authenticated against the server, the VPN connection is established.
If you have connection problems, check the log file Program FilesOpenVPNlogzeroshell.log. Finally, to verify that the traffic is actually routed and encrypted in the VPN you need to perform a traceroute operation at a remote host: if the first hop that is reported belongs to the remote LAN (by default the VPN box has the IP 192.168.250.254), you are sure that the VPN works as you expect. Windows Mobile has not a traceroute utility and therefore you need to install one. A free software to make network debugging is ceNetTools with which you are able to make the traceroute, the ping and whois operations.
Download Openvpn Client For Mac
The command line of OpenVPN
If the system you are using has not a Graphical User Interface for OpenVPN, you have to use the OpenVPN's command line. This can also be used in the case in which you want to automatically start the VPN by using the startup scripts. By typing the command man openvpn from a Unix shell, the OpenVPN's manual page will be displayed. A great number of parameters are available to directly use in the command line prefixed by two consecutive hyphens (–). The same parameters (not prefixed by –) can also be specified in the configuration file. Except for a few cases, it is better to specify the parameters in a configuration file rather than having them in a too long and heavy to read command line.
This section does not examine the parameters because they are already listed and described in the manual page of OpenVPN, but it only describe how to establish a VPN with a Zeroshell OpenVPN server by using the command line:
- Put the files zeroshell.ovpn and CA.pem in a same directory (suppose /etc/openvpn/). For details about how to obtain these files, read the section The configuration file of OpenVPN;
- Edit the configuration file zeroshell.ovpn replacing zeroshell.example.com with the IP address or hostname of the VPN server;
- Change the current directory to /etc/openvpn/ and exec (with root privileges) the command:openvpn –config zeroshell.ovpnAt this point, you are requested for the Username and the Password (look at the Note *). If the client is authenticated against the server, the VPN connection is established.
Best Openvpn Clients For Mac
Build and install OpenVPN
For the most operating system in which OpenVPN works, binary packages already compiled exist. Anyway, sometimes, above all for some Linux Distributions, you could need to build OpenVPN by starting with the source code. Below, it is described how to build OpenVPN:
- Download the OpenVPN's source code from the site http://openvpn.net. Pick the latest stable release that is available (suppose the release 2.0.9 in the rest of this document);
- Extract the files which are stored in the zipped archive that you have downloaded by using the tar command in the following manner:
tar xvfz openvpn-2.0.9.tar.gz - Change the current directory to openvpn-2.0.9 with the command:
cd openvpn-2.0.9 - Check the system and produce the Makefiles by using the following command:
./configure –prefix=/usrIf the ./configure procedure claims that the lzo libraries and headers are not found in the system, install the lzo compression software as follows below:
- Download the source package of LZO from the site http://www.oberhumer.com/ and extract its content with the command:
tar xvfz lzo-2.02.tar.gz - Change the current directory to lzo-2.02 and install the LZO software with the commands:
- ./configure
- make
- make install (This command needs to be executed with root privileges to write in /usr)
Once installed the lzo libraries and headers, came back to the directory openvpn-2.0.9 and launch again the command
./configure –prefix=/usr - Compile the source code with the Makefiles you have just created by using the command:
make - Install the binary program openvpn and its manual pages with the command:
make installBecause the files will be written below the system directory /usr, the last command must be executed with root privileges.
Notes
Openvpn Download
(*) The manner in which the users are authenticated depend on the OpenVPN server configuration. Zeroshell supports a multi-domain authentication system in which you have to configure the authentication source which can be a Kerberos 5 KDC (local, external and trusted) or an external RADIUS server. One of these authentication domains is set to be the default domain. The users of the default domain do not need to specify the username in the form of username@domain (ex. fulvio@example.com). Notice that the domain name is not case sensitive, because if the domain is configured to be a Kerberos V realm, it is automatically converted to uppercase.
